Cyberattacks are growing more advanced every year. A weak server can expose your business to massive risks.
According to IBM’s Cost of a Data Breach Report 2024, the average cost of a data breach has risen to $4.88 million globally. Businesses cannot afford weak server security, yet many still lack a proper security plan.
As Charles Bender, CEO of Attentus Technologies, says “Most cyberattacks exploit simple security gaps. If businesses implement strict server protections, they can prevent most threats before they happen.”
This guide will walk you through the key strategies for securing server systems, protecting sensitive data, and keeping attackers out.
Protect your server infrastructure with expert security solutionsClose security gaps, enforce compliance, and prevent cyber threats before they impact your business. |
Common Threats That Impact Server Security
Cybercriminals use different techniques to compromise servers. Understanding the biggest threats can help you build a stronger security defense.
DDoS Attacks and How to Prevent Them
A Distributed Denial-of-Service (DDoS) attack overwhelms your server with excessive traffic, causing slowdowns or complete failure.
According to CloudSecureTech, the average cost of a DDoS attack for businesses was estimated at $408,000 per incident. These attacks disrupt operations and can lead to data loss.
- Use firewalls and DDoS protection services to filter malicious traffic.
- Implement rate limiting to restrict excessive requests from a single source.
- Deploy cloud-based mitigation services that detect and block large-scale attacks automatically.
Code Injection and Cross-Site Scripting (XSS)
Cybercriminals exploit weak code to inject malicious scripts into servers. This allows them to steal data, manipulate applications, or gain unauthorized access.
- Regularly update software to fix security vulnerabilities.
- Use input validation to prevent malicious scripts from executing.
- Enable web application firewalls (WAFs) to block harmful requests before they reach the server.
Weak Passwords and Misconfigured Firewalls
81% of company data breaches are due to poor passwords. Simple passwords and poor firewall settings make it easy for attackers to break in.
- Enforce complex passwords with multi-factor authentication (MFA).
- Set strict firewall rules to control access and block unauthorized traffic.
- Disable unused ports and services to reduce entry points for attackers.
Best Practices for Securing a Newly Deployed Server
When setting up a new server, security should be a top priority. Attackers actively scan for vulnerable systems and can compromise unprotected servers in minutes.
You reduce risks and ensure a resilient infrastructure by implementing strong security measures from the start.
Below are key steps to secure your server effectively.
Keep Your Server Updated
Outdated software is one of the most common entry points for cyberattacks. Hackers often exploit known vulnerabilities in operating systems, applications, and firmware.
Keeping your server updated ensures that security flaws are patched before attackers can take advantage of them.
- Apply security patches immediately: As soon as updates are released, install them to fix known vulnerabilities.
- Enable automatic updates: Configure automatic updates where possible to avoid delays in patching critical issues.
- Subscribe to vendor security alerts: Stay informed about new threats and recommended updates from your software providers.
- Use patch management tools: These tools help automate and track updates across multiple servers, ensuring nothing gets overlooked.
- Remove outdated software: Regularly audit installed applications and eliminate any unsupported or unnecessary programs that may introduce security risks.
Keeping your server updated improves security and enhances performance and stability over time.
Setting Up a Strong Firewall for Maximum Protection

A firewall acts as the first layer of defense, controlling incoming and outgoing traffic. When not properly configured, unauthorized users and malicious bots can access sensitive data or exploit vulnerabilities.
Start by blocking all unnecessary traffic and only allowing what is essential for your operations. This reduces the attack surface and minimizes exposure to threats.
- Restrict remote access: Allow only specific IP addresses to connect remotely, reducing the risk of unauthorized logins.
- Use an intrusion detection system (IDS): IDS tools monitor traffic and alert administrators about suspicious activity.
- Implement network segmentation: Separate environments (such as databases, web servers, and internal networks) to limit access and contain potential breaches.
- Use geofencing rules: Block connections from high-risk regions known for frequent cyberattacks.
- Regularly review firewall rules: Security threats evolve, so update firewall rules frequently to keep pace with new risks.
A well-configured firewall significantly reduces the risk of intrusions and unauthorized access.
The Importance of Secure Passwords and Multi-Factor Authentication
Strong passwords alone are no longer enough to protect servers from unauthorized access. Cybercriminals use brute force attacks and credential stuffing to gain control of systems. Enhancing security with multi-factor authentication (MFA) and strict password policies can make it significantly harder for attackers to succeed.
- Enforce MFA for all admin accounts: MFA requires an additional verification step (such as a mobile app code or hardware token), making unauthorized logins more difficult.
- Use a password manager: These tools generate and store complex passwords, preventing the reuse of weak or easily guessable passwords.
- Change default credentials: Many servers come with default usernames and passwords, which are commonly exploited by attackers. Replace them immediately.
- Disable root access for SSH: Direct root logins should be disabled to prevent privilege escalation attacks. Instead, use a separate user account with restricted access.
- Implement account lockout policies: After multiple failed login attempts, lock accounts to prevent brute force attacks.
- Monitor login attempts: Set up alerts for unusual login activity to detect and respond to potential threats in real-time.
You make unauthorized access significantly more difficult and protect your server from credential-based attacks when you enforce these measures.
| More articles you might like |
Advanced Strategies for Securing Linux Web Server and Windows 10 Server
A well-secured server environment is critical to protecting sensitive data, preventing cyber threats, and ensuring smooth operations.
While securing Linux web servers and Windows 10 servers require different approaches, each has unique security advantages.
Why Securing a Linux Server Offers Better Protection
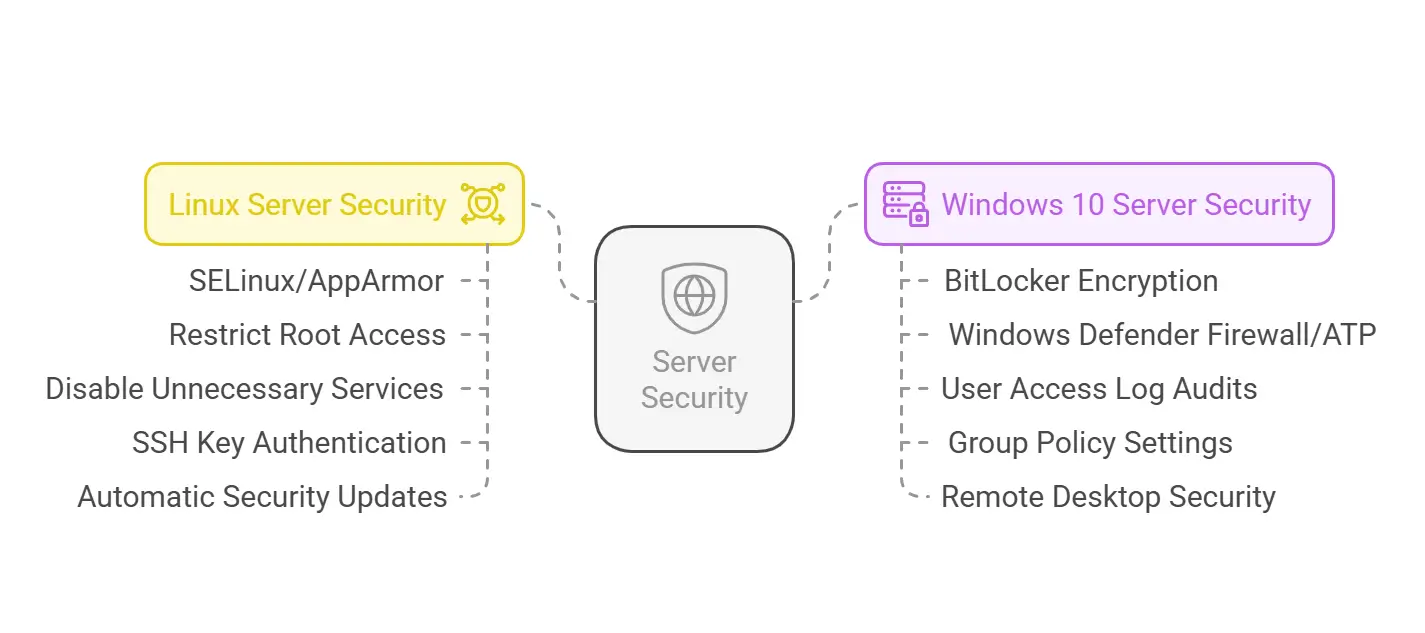
Many organizations prefer securing a Linux server because Linux-based systems offer stronger security controls compared to Windows. The open-source nature of Linux allows administrators to customize security settings, enforce strict access policies, and apply rapid security patches.
To improve security:
- Enable SELinux or AppArmor: These mandatory access control frameworks restrict unauthorized system modifications.
- Restrict root access: Use sudo privileges instead of logging in as root to limit potential damage from security breaches.
- Disable unnecessary services: Running only essential services reduces attack surfaces and lowers the risk of exploits.
- Use SSH key authentication: Replace password-based logins with SSH keys for enhanced access security.
- Enable automatic security updates: Keeping Linux systems updated helps mitigate vulnerabilities before attackers can exploit them.
By applying these best practices, securing a Linux server becomes more effective at defending against modern threats.
Key Steps for Securing Windows 10 Server Environments
While Windows 10 server environments include built-in security tools, proper configuration is essential to prevent unauthorized access and data leaks.
Hackers often target Windows-based systems due to their widespread use in corporate networks.
To strengthen security:
- Enable BitLocker encryption: Protects stored data by encrypting entire disk volumes, making it harder for attackers to access sensitive files.
- Use Windows Defender Firewall and Advanced Threat Protection (ATP): Built-in security tools provide real-time threat detection and malware defense.
- Regularly audit user access logs: Reviewing logs helps identify suspicious login attempts and unauthorized privilege escalations.
- Implement Group Policy settings: Restrict administrative privileges and enforce security policies across the network.
- Enable remote desktop security: Use network-level authentication (NLA) and enforce strong passwords to prevent unauthorized RDP access.
A properly configured Windows 10 server significantly reduces security risks and enhances protection against cyber threats.
VPNs and Private Networks as a Security Measure
Remote access introduces security challenges, making it essential to use VPNs and private networks to prevent unauthorized access. VPNs encrypt internet traffic, ensuring secure data transmission even over public networks.
To enhance network security:
- Use VPNs to encrypt data: This protects information from eavesdropping and unauthorized interception.
- Set up private IP ranges: Restricting public exposure minimizes the attack surface.
- Implement Zero Trust policies: Require identity verification before granting access to internal resources.
- Segment networks for added security: Isolating critical systems prevents lateral movement in case of a cyberattack.
A well-implemented private network strategy ensures that only authorized users can securely access sensitive systems and data.
Server Security Checklist for Businesses
Use this table to ensure your business follows best practices for securing server environments.
| Security Measure | Why It Matters | How to Implement |
| Regular Updates | Patches known vulnerabilities | Enable automatic updates |
| Strong Firewall Rules | Blocks unauthorized access | Define strict traffic rules |
| MFA for Admins | Prevents account hijacking | Require two-factor authentication |
| Secure Backup Strategy | Protects against data loss | Use encrypted offsite backups |
| Log Monitoring | Detects suspicious activity | Set up real-time alerts |
Take Your Server Security Seriously with Attentus Technologies Cybersecurity
Securing your server infrastructure is critical to preventing cyber threats. By updating software, enforcing firewalls, and securing physical access, you can reduce risks. Using advanced protections like encryption and VPNs further strengthens defenses.
| Discover Advanced Cybersecurity Services Across the Pacific Northwest | ||
|---|---|---|
| Bellevue | Seattle | Tacoma |
Attentus Technologies has over 22 years in business serving the Pacific Northwest, a 98.4% CSAT rating, and a 1.2-minute average call-answer time. Our experts provide comprehensive server security solutions to protect your I.T. environment, with a 15-minute average resolution time for common security and compliance issues and a 10-year client retention rate—built on our core value of building trusted relationships. Contact us today to schedule a security assessment and strengthen your defenses.


