
What is a Virtual CIO (vCIO)?
A virtual CIO (vCIO) does everything an in-house chief information officer does, but virtually. Instead of hiring a CIO, you can outsource IT service providers to perform their duties

A virtual CIO (vCIO) does everything an in-house chief information officer does, but virtually. Instead of hiring a CIO, you can outsource IT service providers to perform their duties

You probably already know how important it is to secure information on your computer system. However, a common mistake is assuming that cybersecurity is only needed on a device-level.

Cloud migration is the process of moving your on-premise data to a cloud environment. Alternatively, the cloud migration process may involve moving your data from one cloud service to

The recent increase in cybercrime is leading more and more businesses to invest in cyber insurance policies. Are you considering cyber insurance to protect your business? If so, do you

Hint: The answer lies in selecting the right partner, right from the get-go Partnering with an I.T. managed services provider (MSP) makes good business sense. If successful, you’ll reduce your
As a small to medium sized business (SMB) owner, you understand the importance of protecting your company’s digital assets. You probably know that cybersecurity for your SMB matters, but may

Information technology is quickly becoming more of a necessity. The more technology intwines itself into business, the more crucial it is to your business goals. As a result, the line
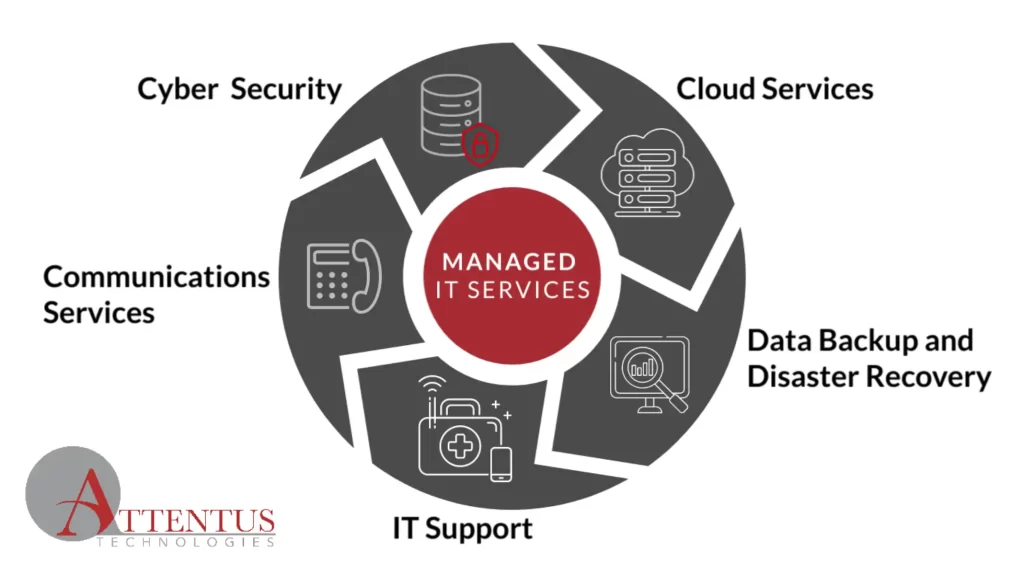
As more American businesses trust their tech to a managed service provider (MSP), it’s important to understand the range of services they offer. Most MSPs offer several different types of

Business owners have a lot on their minds. One of their top priorities is dealing with cyber attacks. An unprecedented 57% of respondents to the 2022 Travelers Risk Index survey

If there is one item that constantly makes national and international headlines, it’s security and data breaches experienced by prominent companies, websites, and service providers.

They look great on paper, but why do so many cyber security plans fail? Without a well-formulated cyber security implementation plan, 2 out of 3 CIOs doubt their organization’s security

You’ll lose as much as $9,000 per minute during the course of unplanned network downtime. This issue, however, is preventable with the appropriate IT services supporting your business. But the natural question