Creating a cyber security strategy is no longer a luxury but a necessity for any growing business. With cyber threats evolving daily, businesses must proactively secure their data, operations, and client information. Whether you’re a small company or scaling up, having a solid cybersecurity plan in place can mean the difference between thriving and surviving.
Here’s a sobering statistic: 60% of small businesses that suffer a cyberattack go out of business within six months. This alarming figure underscores the devastating impact of inadequate security measures. No business, regardless of size, is immune to cyber threats.
As Charles Bender, CEO of Attentus Technologies, states, “The cost of prevention is far less than the cost of recovery. Every business leader must treat cyber security as a core business strategy.” The takeaway here is clear: businesses that invest in a strong I.T. security roadmap are not just protecting themselves from threats—they are investing in long-term resilience.
In this blog, we’ll explore how to build a comprehensive cybersecurity strategy, including actionable steps for risk management, system updates, and employee training, to ensure your business stays secure as it grows.
Safeguard Your Business with a Strong I.T. Security RoadmapBuild a proactive cyber security strategy that protects your business from evolving threats |
Understanding the Cyber Threat Landscape for Growing Businesses
1. The Rise in Cyber Attacks Against Small Businesses
With cybercriminals increasingly targeting smaller organizations, it’s crucial to understand the growing threat landscape.
In 2023, there were 2,365 reported cyberattacks, affecting over 343 million victims globally. Small businesses often don’t realize they are high-value targets for these attacks. The absence of advanced security measures makes them more vulnerable than larger corporations. As businesses scale, this threat only grows, highlighting the need for proactive protection.
Recognizing these risks allows businesses to take steps that prevent attacks from causing long-term damage. The image below details key vulnerabilities in small businesses, and some measures to counter these.
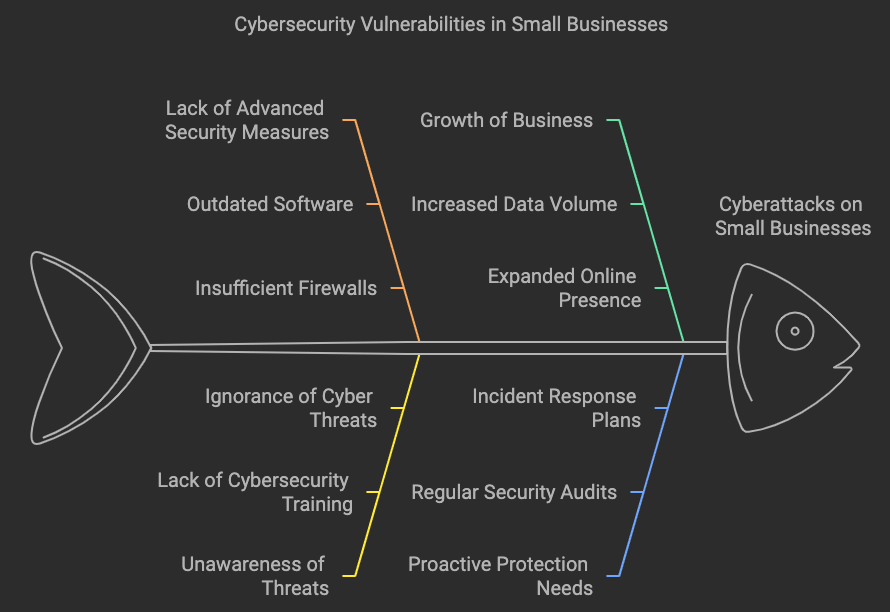
2. Why Hackers Target Growing Businesses
Hackers target businesses that are growing because they often lack sophisticated defenses. Rapid expansion often means systems and processes don’t scale securely, leaving vulnerabilities.
Smaller organizations may not have the financial or technical resources to build comprehensive security systems early on. This gap in security creates a prime opportunity for cybercriminals. Additionally, growing companies handle more data as they expand, increasing their risk profile.
Investing in a tailored cyber security strategy at this stage is essential to close these gaps before they are exploited.
3. The Human Element in Cyber Threats
One of the most overlooked components in cybersecurity is the role of human error. Phishing emails, accidental data leaks, and untrained employees create significant vulnerabilities.
According to studies, many cyberattacks could have been prevented through better staff awareness. Surprisingly, despite the rising number of attacks, only 26% of small business owners have cyberattack insurance, leaving them financially exposed.
Educating your employees about cybersecurity best practices can mitigate many risks, making your team the first line of defense against cyber threats.
Key Components of a Comprehensive Cybersecurity Plan
1. Risk Assessment and Prioritization
The foundation of a successful cybersecurity plan starts with a detailed risk assessment.
This process involves identifying the most critical areas of your business, such as financial data or intellectual property. By understanding what’s at stake, businesses can prioritize protection efforts based on risk level. High-priority areas should receive the most immediate attention to mitigate any potential damage.
This evaluation also helps companies identify existing security gaps that might be overlooked. Without a clear understanding of risk, cybersecurity efforts may miss critical vulnerabilities.
2. Multi-Layered Security Measures
A solid cyber security strategy involves more than a single layer of defense. It requires a blend of tools, including firewalls, intrusion detection systems, encryption, and multi-factor authentication.
Each layer addresses different types of threats, making it harder for cybercriminals to gain access. Layered security measures work together to create a comprehensive defense system. By using multiple barriers, businesses reduce the likelihood of a successful attack.
No single tool is foolproof, but by combining several, you significantly strengthen your overall protection.
3. Leveraging Managed I.T. Services for Protection
Partnering with managed I.T. services can take your cybersecurity to the next level.
Managed service providers (MSPs) offer expertise, resources, and 24/7 monitoring that many growing businesses can’t afford to maintain in-house. With 64% of businesses now using managed I.T. services, the benefits are clear: access to cutting-edge security technologies, expert advice, and faster responses to potential threats.
MSPs continuously update security measures and stay ahead of emerging threats. By leveraging their support, businesses can focus on growth while experts manage their security.
| Explore More Cybersecurity Guides |
|---|
Creating an I.T. Security Roadmap for Long-Term Protection
1. Aligning Security with Business Growth
Your I.T. security roadmap should be built to grow alongside your business.
As your company expands, your security requirements will also evolve, requiring continuous adjustment. It’s important to regularly evaluate how your cybersecurity measures are keeping pace with your growth. Whether you’re onboarding new employees or entering new markets, your security needs to scale accordingly.
This alignment ensures that your business is always protected, even as new challenges arise. A proactive approach to aligning security with growth will mitigate risks before they become significant issues
2. Budgeting for Future Cybersecurity Needs
Many businesses mistakenly see cybersecurity as a one-time cost, but it’s an ongoing investment.
As new threats emerge and your company grows, your security budget needs to adapt. Planning for future cybersecurity expenditures helps prevent surprises down the road. Make room in your financial strategy for system updates, employee training, and new technologies that can keep you ahead of threats.
Without dedicated resources, businesses risk falling behind in their defenses. Budgeting ensures your company remains prepared for whatever cyber risks the future may bring.
3. Staying Ahead of Emerging Threats
Cyber threats are constantly evolving, and staying ahead requires regular updates to your security strategy.
Emerging technologies like AI-driven cyberattacks pose new challenges that require innovative defenses. Regular security audits can help identify weaknesses that weren’t apparent during the initial implementation of your plan. By continuously monitoring and upgrading your systems, you reduce the chances of being caught off guard by a new threat.
The businesses that are most successful in defending against cyberattacks are those that maintain an agile and proactive approach to security.
Table: Cybersecurity Essentials for Growing Businesses
Here is a quick comparison of key cybersecurity components every growing business should consider to protect its assets and operations.
| Cybersecurity Component | Description | Importance |
| Risk Assessment | Identifying vulnerabilities in your systems and processes. | Crucial for prioritizing resources and responses. |
| Multi-Factor Authentication | An extra layer of security requiring more than one form of verification. | Reduces risk of unauthorized access. |
| Data Encryption | Converting data into a secure format to prevent unauthorized access. | Protects sensitive information from breaches. |
| Employee Training | Educating staff on recognizing and avoiding cyber threats like phishing. | Minimizes human errors leading to breaches. |
| Managed I.T. Services | Outsourcing cybersecurity to experts for ongoing monitoring and updates. | Provides 24/7 protection with advanced tools. |
Staying informed about these cybersecurity essentials ensures your business remains secure as it grows. Implementing these measures early will strengthen your defenses and help prevent costly cyberattacks.
Transform Your Cybersecurity With Specialized Solutions from Attentus Technologies
When securing your business, generic solutions won’t cut it. With over 20 years of experience in safeguarding our partners’ most valuable assets, we focus on delivering personalized, results-driven cybersecurity that adapts to your unique challenges.
Our approach ensures your operations stay resilient against evolving threats, all while integrating seamlessly into your business strategy.
| Discover where you can find our cybersecurity services to safeguard your business | ||
|---|---|---|
| Seattle | Bellevue | Tacoma |
Contact us and partner with a company that understands the value of protection that works for you—without the hassle.

