To combat the rising number of sophisticated cyber threats, a meticulously designed cybersecurity plan is no longer a luxury—it’s a necessity for ensuring the safety and continuity of your business

They look great on paper, but why do so many cybersecurity plans fail? Many CIOs are leery of their organization’s security readiness without well-formulated cybersecurity implementation plans.
For example, statistics show that while 92% of cybersecurity decision-makers say their organizations increased their security budgets, only 40% were confident that their preparations gave them enough resources and tools to comply with cybersecurity regulations. And then 19% admitted that they had done very little to prepare for threats they would face.
In this blog, we’ll help you understand a cybersecurity implementation plan and guide you step-by-step through implementing one in your business. This way, you can learn to keep your organization safe while staying miles ahead of your competitors.
What is a cybersecurity implementation plan?
A cybersecurity implementation plan is a strategic roadmap outlining measures to safeguard digital assets, networks, and systems from cyber threats such as malware and phishing.
It identifies the potential risks, outlines the necessary controls and processes, and assigns roles and responsibilities to employees. This plan is crucial for your business to protect its valuable data and ensure continuity in the face of ever-evolving cyber threats.
9 steps for implementing a cybersecurity plan at your business
Sound cybersecurity is necessary to prevent your business from being hurt by “bad actors.” Lax security can lead to data breaches, money loss, disruption to operations, and a damaged reputation in your customer base and professional community.
Here are nine steps that will help you build an effective cybersecurity implementation plan:
Step 1: Build a checklist
A well-defined cybersecurity policy serves as the foundation of your cybersecurity strategy. However, realizing it in the real world requires a step-by-step approach. Start by developing a checklist with the big and little things you need to accomplish. Your checklist should:
- Involve conducting a security risk assessment.
- Evaluate if your current technology is up to the task
- Select a security framework
- Provide clear goals for your team
- Outline KPIs to measure the success of the efforts
- Identify mission-critical I.T. systems
- List key activities, such as patching
- Identify people responsible for each action item
Preparing a checklist makes allocating tasks among your team members much easier and allows you to verify if they have been completed as intended.
It’s also worth checking out the government-run Cybersecurity and Infrastructure Security Agency (CISA) SAFECOM guide, helping organizations implement an effective cybersecurity risk assessment.
Assess your current cybersecurity posture
This involves taking stock of your I.T. infrastructure, hardware, software, network, and data storage systems. Perform a risk assessment to understand which aspects need immediate attention and allocate resources accordingly in your cybersecurity implementation plan. Overall, the risk assessment tries to predict the likelihood of a security breach and its impact on your business.
Prioritize mission-critical areas of your I.T. infrastructure, such as the business network and data storage.
Besides strengthening your defensive posture, a risk assessment can help save you money and downtime by anticipating attacks and mitigating vulnerabilities. It can also help ensure that you are compliant with relevant data-safety regulations.
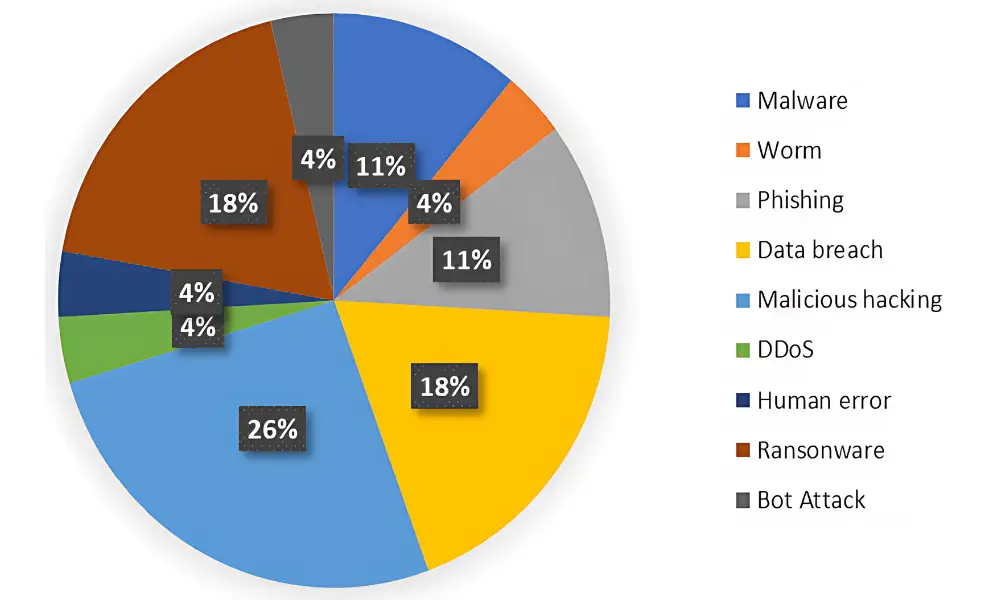
ResearchGate: Common types of cyberattacks
Step 3: Define your cybersecurity goals
With a clear understanding of your current cybersecurity state, it’s time to define your goals. These goals will guide your strategy and help you prioritize which areas to focus on. Some common goals include:
- Protecting sensitive data
- Ensuring business continuity in the face of cyber threats
- Compliance with industry regulations and standards
- Building customer trust and confidence in your organization’s security
Defining KPIs for each of these goals is essential for evaluating the success and effectiveness of your security strategy. One approach is to assign letter grades to the cybersecurity measures implemented by your suppliers. You can use metrics like Mean Time to Detect (MTTD) to assess your readiness for your organization.
MTTD measures how quickly your I.T. team identifies security incidents, helping to highlight areas for improvement. By reducing detection time, you can respond faster to threats and minimize downtime.
Step 4: Establish a cybersecurity team
Establishing a dedicated cybersecurity team is crucial for implementing and maintaining your cybersecurity program. Depending on your organization’s size and needs, this team can consist of in-house I.T. staff or outsourced cybersecurity professionals.
Assign specific roles and responsibilities to ensure everyone knows their part in maintaining and enhancing your organization’s security posture. You should foster a collaborative environment for best performance and establish clear goals and metrics for success. To prevent the team from getting trapped in its silo, open lines of communication should be set with other departments and key stakeholders.
Step 5: Implement security controls
With your policy in place, the next step is implementing the necessary security controls. These controls should be tailored to your organization’s specific needs and risks and are designed to protect the confidentiality, integrity, and availability of a company’s data and technology. Some examples of security controls include:
- Regular software updates and patches
- Firewalls and intrusion detection systems
- Encryption of sensitive data
- Strong password policies and multifactor authentication
- Regular security audits and vulnerability assessments
- Virtual private networks (VPNs)
Step 6: Tap into the power of AI
Increasingly, companies need to tap into the power of artificial intelligence (AI) for cybersecurity. Microsoft points out that this works “by evaluating massive amounts of data across multiple sources to identify activity patterns across an organization, such as when and where people sign in, traffic volumes, and the devices and cloud apps employees use. Once it understands what’s typical, it can identify anomalous behavior that may need to be investigated.”
Making AI part of your cybersecurity plan is important because hackers are also using the technology to find increasingly sophisticated ways to automate their cyberattacks and break into systems.
Step 7: Train and educate employees
Employee awareness and training are among the most critical aspects of a successful cybersecurity strategy. Offer regular training sessions to educate your staff about the latest threats, best practices for online safety, and your company’s security policies. The key word here is “regular.” Because technology and threats evolve so quickly, it’s important to stay on top of developments.
Encourage a culture of vigilance and empower employees to report any suspicious activities or incidents. Social engineering, such as phishing attacks, relies on the haste and unawareness of employees, so look at wider company practices as well. While there are many external threats to be aware of, often problems are caused by staff mistakes or inattentiveness.
Step 8: Establish an incident response plan
Cyber incidents can still occur even with the best security measures in place. Having an incident response plan ready will help you minimize the impact of a breach and recover more quickly. This plan should outline the steps to take in the event of a cyberattack, including:
- Identifying the affected systems
- Containing and eradicating the threat
- Assessing the damage
- Communicating with stakeholders
- Restoring systems and data
- Learning from the incident and improving data protection
Step 9: Monitor and review your strategy
Your cybersecurity strategy should be a living document that evolves as your business grows and the threat landscape changes. Regularly review and update your security and risk management plans to ensure they remain effective in protecting your organization from new and emerging threats.
This might involve performing regular security audits, penetration testing, and revising your policies as needed.
Develop a more effective cybersecurity strategy and implementation plan
Effective information security without burdening workflows — that’s why businesses have trusted us for overtwo decades. Work with the seasoned cybersecurity professionals of Attentus to deploy proven data-saving and business-saving technologies across your organization. Be the Answer is one of our core values: we own the problem and hold ourselves accountable. Accountability means there’s no finger-pointing or blame-shifting. We take ownership every time and partner with all stakeholders to find the best solution, ensuring that your cybersecurity needs are met with the utmost professionalism and expertise.
Find out how we help organizations like yours implement I.T. security plans seamlessly and successfully defend against serious threats. We aim to deliver exceptional results every time.
